Disclaimer: despite the date, this is *not* a joke.
Over the weekend, we started noticing a number of projects had a message added to their Project web pages that stated:
“This is a project whose homepage has been hacked with the SourceForge backdoor by a 1337 hacker…”
Upon investigating we found that the affected projects had configuration files (which contained database usernames and passwords) that were world readable. In other words, anyone looking in the right place could get these usernames and passwords and have direct access to the database.
Setting proper permissions
To protect these passwords, we need to make sure that the permissions are set correctly. There’s already a ton of information around the web on basic UNIX style permissions, so in short, the web server uses the “group” permission, so that needs to have read permissions for the configuration file (g+r), but nobody else should (0-r). Generally speaking, for most config files, value you want is “rw-r—–” (or 640).
For further reading, see our Project web filesystem permissions doc.
Filezilla
You can change the filesystem permissions in a variety of ways. Using the graphical sftp client FileZilla for example, you can navigate to the file, right click it and select “File Permissions”.
Shell or sftp command line
Or you can use “chmod” over command line sftp or the Shell Service:
sftp> chmod 640 /home/project-web/strawhat/htdocs/myawesomeapp/passwords.php
Changing mode on /home/project-web/strawhat/htdocs/myawesomeapp/passwords.php
sftp>
Resetting DB passwords
Once the file permissions are set correctly, you should reset your project database passwords and update your config files accordingly.
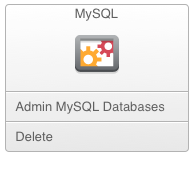
To update your passwords on the New SourceForge (aka Allura) system, go to Admin -> Tools, on MySQL card, “Admin MySQL Databases”
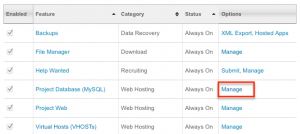
On the Classic SourceForge system, go to Project Admin -> Feature Settings, in “Project Database (MySQL)” row, select “Manage”
Other ways to protect yourself
- Keep your SourceForge site credentials secure. Following standard best practices, ie., using secure passwords and don’t reuse passwords on multiple sites
- Only add trusted users to Project Administrators
- Keep your application up to date, especially for security fixes
- Maintain regular backups
If you need further help with this, please let us know.


After checking 850 projects, I’ve 44 hacked your projects, but you were lucky! I did this to notify the project owners so that they would fix the issue.
If other hackers did this, they might not have been so nice. They might plant malicious scripts or even just drop your data for fun.