When you download a file from SourceForge (or, indeed, from anywhere), there are often mechanisms for verifying that you’ve downloaded the right thing – ie, that nobody has tampered with the file, and that you’re getting what the developers intended for you to download.
The most common way to do this is with a file hash that gets generated with the file is created.
Verifying downloaded files
Each time a file is uploaded, we generate an MD5 hash, and a SHA1 hash of that file, so that you can quickly check whether a file has been tampered with.
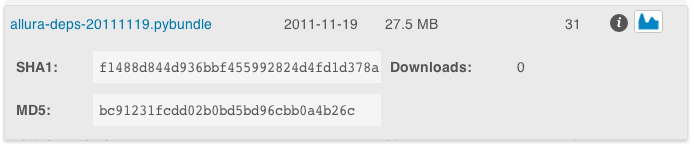
In the files interface, click on the “I” information icon next to the file, and you’ll see, as in the image above, two strings labelled SHA1 and MD5. These are cryptographic strings generated from the file itself, which you can verify on your end to ensure that the file you are downloading hasn’t been tampered with somewhere between us and the mirror, or between the mirror and you.
We will also, very soon, be adding those checksum strings to the file download page itself, so that you don’t have to go out of your way to look for it.
Once you have downloaded the file, check to see that the MD5 checksum, or SHA1 checksum, of that file, matches what we list on the site. If they don’t match, notify us, then try downloading from a different mirror.
On Windows, we recommend a tool like md5deep to generate the hashes from the downloaded file. There are also browser plugins that will calculate the checksums on a file as you download it, so that you’re less likely to forget to do it yourself.
On Linux, at the command line:
$ md5sum download.tar.gz 84a3d6aa561b112058ad9aa08a352044 download.tar.gz $ sha1sum download.tar.gz b6133cbc973faf908f83fa950574db0fa268480c download.tar.gz
On Mac OS X, at the terminal:
$ md5 download.tar.gz MD5 (download.tar.gz) = 84a3d6aa561b112058ad9aa08a352044 $ shasum download.tar.gz b6133cbc973faf908f83fa950574db0fa268480c download.tar.gz
Again, if you discover that a checksum doesn’t match, please tell us so that we can do something about it as quickly as possible.
We also strongly encourage project admins to verify your files yourselves on various mirror servers, after you’ve uploaded them, ensuring that what’s on the server matches what you uploaded.
@_cypherpunks_ @sourceforge good idea, but does not help against manipulated source files
@saltlet Yeah, that’s very true. No silver bullet on that one.
Is there a direct link to get that information to automate the download process?
tremblaysimon The only place where we (SourceForge) display this is in the files interface as described above. Also, quite frequently, individual projects will choose to post file hashes on their own websites.