I am disappointed from properties of VeraCrypt which I have chosen to use on my new PC on disk Samsung 960 Pro 512 GB that has transfer speeds of 3500MB/s read and 2100MB/s write. After encrypting the drive on Windows 10 the speed dropped rapidly only to 550 MB/s read and 1000 MB/s write even though I used AES method where VeraCrypt tells me it can do 7.7 GB/s. The mentioned drive was very expensive and encryption is mandatory for me so I'm asking if my money for this super fast Samsung drive went to waste? Do you have any solution? Thank you for your reply.
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
I have the same issue with a Samsung 960 EVO 512 GB and I am also looking for an explanation for this phenomenon. The processor is by far fast enough to enrypt decrypt without the drive having to take a performance hit.
I went looking for M.2 NVME settings in the BIOS and System preferences and also for any setting in Veracrypt itself which might negatively affect the performance but so far no luck.
Does anyone have any helpful input on this? Is it to be expected?
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
I discussed the problem with Idrassi .Probably I can solve the problem but for me personally it is not vital. EFI support and hidden OS for EFI were done because I need it. And I shared my results with community. It took much effort and created some difficulties. Almost no compensation/profit.
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
you raise some very valid points. what would you request for compensation? these are some of the most popular m2 drives in the world and the new versions are to be released shortly, so this would be truly beneficial to the end user.
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
I get it. Veracrypt's technology has become so complex, that only the best and brightest people have the skills necessary to work on it. And it makes no sense to do it for free considering how valueable / highly compensated that person's time is.
Thank you for Idrassi and Alex for all your contributions.
Would it be possible to add the speed issue to known list of problems / limitations?
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
Comparison of VeraCrypt and DiscCryptor on SSD:
As you can see, the performance is practically not degraded by DiscCryptor, but on VeraCrypt the performance drops in many times.
Donation is good way to support the project but I have to note: I do not know details about current donation level of VeraCrypt and I got 100 euro only for last half a year...
With all the respect, we who use VeraCrypt with DCS should all provide some help and gratitude to people who are behind it.
@Alex, I guess your https://sourceforge.net/p/dc5/tickets/1/ is swamped and not really visible to too many people, hence it doesn't get attention. On top of this value of BTC has been changing highly over the time and as result at one point in time the said 2BTC was worth 34k$? :)
We might be facing chicken and egg situation, where maybe VeraCrypt is not that well known for typical user because of technical difficulties behind full system encryption. All technical elements to build great and well secured system are here, with very flexible options but aimed at highly skilled technical user.
How about if VeraCrypt with DCS could do something similar like kickstarter project where on the offer would be an easy to use tool for full system encryption, with dual systems, boot, etc. offering it that way, would first reassure that if some work would to be put into that it would be rewarded at expected level seen and set upfront and everyone would know in advance what to expect by fundraising activity.
With that said it might look like upside down as we have already great VeraCrypt and DCS, but the trick with it is that it is relatively difficult to set it up for fullsystem encryption with two systems, etc.
To backsupport my personal interest and gratitude to people involved, whilst not with BitCoin I'd be interested how to send over some $ as a way of thank you for what has been done.
If we all would do that, it would certainly be a good motivator for everyone behind the great VeraCrypt and DCS.
@Alex, silly question - but how to send you some small $ as way of thank you?
Thanks,
Dawid
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
Main reason for creating DCS is to check interest from community. Not only donations - votes, proposals etc. Result is small.
I started campaign at Pledgie in addition to BTC address - no result. BTC is good way because it is easy to check. For anonomous transfers it can be Monero (XMR) -
43W4Xz5Qe5E4jRbjND79d2f8knFo2nQVs52rP384LFDxVd7c3pLUTFpQ6awqHUoM3AHicC5CPHAoLJKMmukajKTnFcp5MwT
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
VeraCrypt is old and complex project. It requires regular work but current situation - slow step by step according to resources.
Performance problem - several months of full time work. (research, PoC, beta, release)
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
I'm having the exact same problem, also about 45MB/s maximum. It's a shame, really, as there's no alternative to VeraCrypt as far as I know... and using the SSD encrypted is wasted money on the SSD.
With SSDs getting more and more widespread I really wonder why this hasn't been fixed yet. :(
Also I've noticed I have 100% disk activity while only writing at a few MB/s with a response time of 2000-3000ms. Is this also related to VeraCrypt?
Last edit: wat 2018-12-02
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
It hasn't been fixed as great guys need to have a life too.
With that said, if it could be valued and I.e. project created on
Kickstarter with given value, it would be transparent for donators how
much money is needed and show if it is being reached or how far are we from
paying for their great work.
On Sun, 2 Dec 2018, 13:11 wat <radieo@users.sourceforge.net wrote:
I'm having the exact same problem, also about 45MB/s maximum. It's a
shame, really, as there's no alternative to VeraCrypt as far as I know...
and using the SSD encrypted is wasted money on the SSD.
With SSDs getting more and more widespread I really wonder why this hasn't
been fixed yet. :(
Outsside of a benchmark, most people are unlikely to see the difference between using and not using VeraCrypt. The Crystal DiskMark program used is performing 4K random read/writes with 8 different threads. This is essentially a worst case scenario for VeraCrypt, since I suspect VeraCrypt is funelling everything through a single encryption/decryption thread. So the multiple threads in Crystal DiskMark aren't scaling they way they would on a bare SSD.
I cannot come up with a realistic real-world scenario where a user would want to perform random reads or writes on multiple threads simultaneously. Yes, I'm sure you could come up with some sort of interesting database scenario, I could probably come up with a dozen possibilities, but realisticly, outside a benchmark you are likely to even be able to notice the difference.
Also, I canot reproduce the extremely poor random write performance with my SSD. This is my result
The above result is with VeraCrypt and two Serpent(AES()) chained encryption.
In short, yes, there is an issue. It's not serious. It will likely not affect anyone in the real world. Sequential read/write is essentially unaffected. Random read/write is affected, but not as seriously as you might think. And for most users, you won' t notice a thing.
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
How is a decrease from a couple hundreds to 45 MB/s read or even 80MB/s for the write "not serious"? The difference is indeed noticeable. I've tried the SSD again unencrypted and this time the SSD wasn't at 100% disk activity with 50 write or read with response times of 3000ms making the OS quite laggy. Games loaded a tad faster as well. I'd say it is pretty serious.
Last edit: wat 2018-12-03
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
The "decrease" you are seeing on the is just a number printed by a disk benchmark program. Benchmarks are only useful insomuch as they represent what happens in the real world. You are simply looking at those numbers and seeing that one is much higher and you are thinking that represents something better. You have to interpret what the number means for the benchmark to be meaningful.
That number represents the number of random reads of 4kb of data that can occur when using multiple threads. Outside of a disk benchmarking environment, it is highly unlikely you will ever encounter this kind of sustained disk activity in the real world. I can't think of a real-world scenario outside of a server environment where you would want to chain together tens of thousands of individual seek/read operations occuring with multiple threads. Even in a server environment almost all software is designed specifically to avoid that kind of behaviour, so as to avoid thrashing a physical drive.
The only reason that kind of thing is even benchmarked is just to show off what a SSD can do that a physical drive can't. It's a way the benchmark crowd pat themselves on the back.
I do not find my OS laggy in the least. I do not find my game load times are adversely affected. In fact, in Star Trek Online, I find I am consistantly the first one in my team to load and enter a mission, and that is a function mostly of client load time.
I did not say VeraCrypt has zero impact on the performance of an SSD system. Just that this issue will have almost no impact on system speed. For most people and situations outside of a benchmark program it will be essentially unnoticable. I will give that there will always be some performance penalty with VeraCrypt, though. No disk encryption system can get around that. Game engines, if they are well written, are designed to do some of the heaviest CPU work during a level load operation in separate processing threads during times of high disk activity in order to minimize load times on systems that have physical hard drives. This is so that the CPU is staying busy processing the level data it has while a separate thread is collecting more. So VeraCrypt is now contending for CPU usage with games that are increasingly written to take advantage of multiple CPU cores. This is not something that "fixing" the minor issue in the VeraCrypt driver is ever going to address. You simply cannot have disk encryption occur at the speed of an SSD without a CPU performance penalty.
So, I stand by my assessment:
This particular issue of multi-thread random 4K read/write operations-per-second is extremely minor.
This issue will not cause a slowdown that is noticable for any sort of normal desktop computer usage, including gaming
If you are experiencing a noticable lag, especially in a game it is far more likely to simply be an issue of CPU contention that will be common to all WDE systems, and not this issue.
Disk activity at SSD speeds incurs more CPU overhead than for standard drives. This is just a given. Ther is no way around this. However a system with SSD and VeraCrypt will still be an order of magnitude more responsive than a similar system with a mechanical hard drive even without VeraCrypt. But yes, a system with an SSD and VeraCrypt will have some minor performance penalty when compared to the same system without VeraCrypt. This is unavoidable but, in my experience, minor and worth it.
Last edit: Kurt Fitzner 2018-12-03
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
Same problem. This is not about hypothetical benchmarks, but noticable, with the SSD constantly at 100%. When I switched to Bitlocker, the problem went away.
If you would like to refer to this comment somewhere else in this project, copy and paste the following link:
Hello,
I am disappointed from properties of VeraCrypt which I have chosen to use on my new PC on disk Samsung 960 Pro 512 GB that has transfer speeds of 3500MB/s read and 2100MB/s write. After encrypting the drive on Windows 10 the speed dropped rapidly only to 550 MB/s read and 1000 MB/s write even though I used AES method where VeraCrypt tells me it can do 7.7 GB/s. The mentioned drive was very expensive and encryption is mandatory for me so I'm asking if my money for this super fast Samsung drive went to waste? Do you have any solution? Thank you for your reply.
I have the same issue with a Samsung 960 EVO 512 GB and I am also looking for an explanation for this phenomenon. The processor is by far fast enough to enrypt decrypt without the drive having to take a performance hit.
I went looking for M.2 NVME settings in the BIOS and System preferences and also for any setting in Veracrypt itself which might negatively affect the performance but so far no luck.
Does anyone have any helpful input on this? Is it to be expected?
Looks like no one cares about it.
The problem is known. It is internal organization of I/O in VeraCrypt. Rather complex modification.
Do you guys have any plans to improve this? It's going to be more and more of a problem now that NVME SSDs are getting popular.
Maybe you could take a look at how DiskCryptor does it, it doesn't seem to have this problem.
I looked at DiskCryptor. This is the reason - the problem is known. The way to solve is known. Rather complex. Lack of time.
I'm experiencing the same. Are there any news to this? Does @idrassi know?
Thank you!
Last edit: panni 2017-10-18
I discussed the problem with Idrassi .Probably I can solve the problem but for me personally it is not vital. EFI support and hidden OS for EFI were done because I need it. And I shared my results with community. It took much effort and created some difficulties. Almost no compensation/profit.
you raise some very valid points. what would you request for compensation? these are some of the most popular m2 drives in the world and the new versions are to be released shortly, so this would be truly beneficial to the end user.
I get it. Veracrypt's technology has become so complex, that only the best and brightest people have the skills necessary to work on it. And it makes no sense to do it for free considering how valueable / highly compensated that person's time is.
Thank you for Idrassi and Alex for all your contributions.
Would it be possible to add the speed issue to known list of problems / limitations?
Sorry, I did not notice this topic before. I duplicate the post from here :
Last edit: dmitriy a 2018-04-13
I will supplement my message.
Comparison of VeraCrypt and DiscCryptor on SSD:
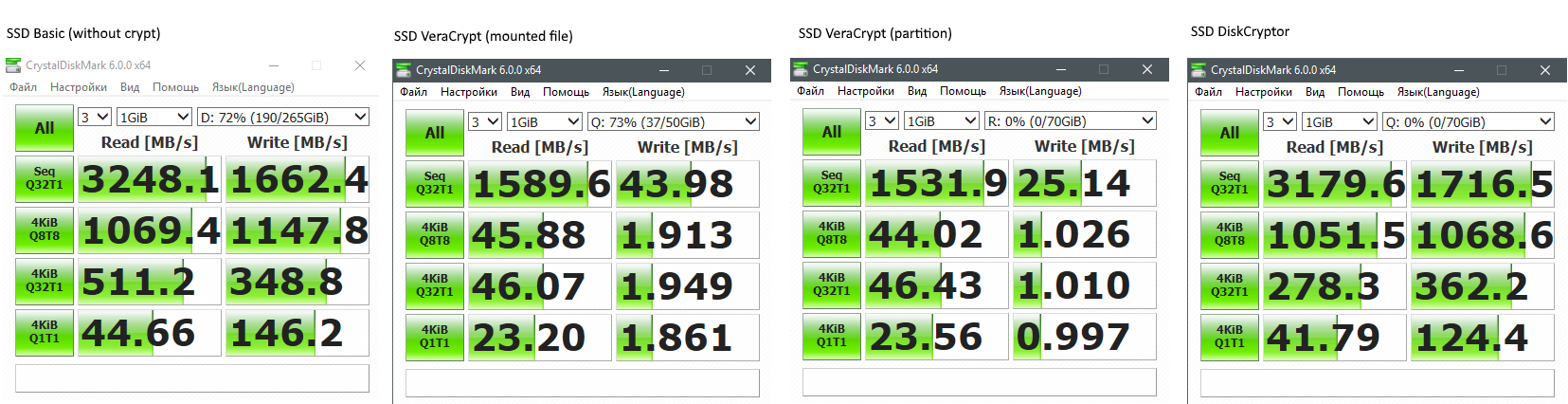
As you can see, the performance is practically not degraded by DiscCryptor, but on VeraCrypt the performance drops in many times.
more info
Last edit: dmitriy a 2018-04-16
Hi dmitriy a,
Donation is good way to support the project but I have to note: I do not know details about current donation level of VeraCrypt and I got 100 euro only for last half a year...
My part is DCS loader (EFI+win driver+installer https://sourceforge.net/projects/dc5/files/beta/)
Year ago I wrote what is necessary to continue but no interest from community - https://sourceforge.net/p/dc5/tickets/1/
Last edit: Alex 2018-04-14
Hi Alex,
Alex, are you familiar with the author of the VeraCrypt? Could you ask him if it is possible to solve this problem?
Hi All,
With all the respect, we who use VeraCrypt with DCS should all provide some help and gratitude to people who are behind it.
@Alex, I guess your https://sourceforge.net/p/dc5/tickets/1/ is swamped and not really visible to too many people, hence it doesn't get attention. On top of this value of BTC has been changing highly over the time and as result at one point in time the said 2BTC was worth 34k$? :)
We might be facing chicken and egg situation, where maybe VeraCrypt is not that well known for typical user because of technical difficulties behind full system encryption. All technical elements to build great and well secured system are here, with very flexible options but aimed at highly skilled technical user.
How about if VeraCrypt with DCS could do something similar like kickstarter project where on the offer would be an easy to use tool for full system encryption, with dual systems, boot, etc. offering it that way, would first reassure that if some work would to be put into that it would be rewarded at expected level seen and set upfront and everyone would know in advance what to expect by fundraising activity.
With that said it might look like upside down as we have already great VeraCrypt and DCS, but the trick with it is that it is relatively difficult to set it up for fullsystem encryption with two systems, etc.
To backsupport my personal interest and gratitude to people involved, whilst not with BitCoin I'd be interested how to send over some $ as a way of thank you for what has been done.
If we all would do that, it would certainly be a good motivator for everyone behind the great VeraCrypt and DCS.
@Alex, silly question - but how to send you some small $ as way of thank you?
Thanks,
Dawid
Hi David,
Thank you for interest to the project.
Main reason for creating DCS is to check interest from community. Not only donations - votes, proposals etc. Result is small.
I started campaign at Pledgie in addition to BTC address - no result. BTC is good way because it is easy to check. For anonomous transfers it can be Monero (XMR) -
43W4Xz5Qe5E4jRbjND79d2f8knFo2nQVs52rP384LFDxVd7c3pLUTFpQ6awqHUoM3AHicC5CPHAoLJKMmukajKTnFcp5MwT
How much money (ballpark) would be needed to get VeraCrypt's performance on par with Bitlocker's ?
VeraCrypt is old and complex project. It requires regular work but current situation - slow step by step according to resources.
Performance problem - several months of full time work. (research, PoC, beta, release)
I'm having the exact same problem, also about 45MB/s maximum. It's a shame, really, as there's no alternative to VeraCrypt as far as I know... and using the SSD encrypted is wasted money on the SSD.
With SSDs getting more and more widespread I really wonder why this hasn't been fixed yet. :(
Also I've noticed I have 100% disk activity while only writing at a few MB/s with a response time of 2000-3000ms. Is this also related to VeraCrypt?
Last edit: wat 2018-12-02
It hasn't been fixed as great guys need to have a life too.
With that said, if it could be valued and I.e. project created on
Kickstarter with given value, it would be transparent for donators how
much money is needed and show if it is being reached or how far are we from
paying for their great work.
On Sun, 2 Dec 2018, 13:11 wat <radieo@users.sourceforge.net wrote:
Outsside of a benchmark, most people are unlikely to see the difference between using and not using VeraCrypt. The Crystal DiskMark program used is performing 4K random read/writes with 8 different threads. This is essentially a worst case scenario for VeraCrypt, since I suspect VeraCrypt is funelling everything through a single encryption/decryption thread. So the multiple threads in Crystal DiskMark aren't scaling they way they would on a bare SSD.
I cannot come up with a realistic real-world scenario where a user would want to perform random reads or writes on multiple threads simultaneously. Yes, I'm sure you could come up with some sort of interesting database scenario, I could probably come up with a dozen possibilities, but realisticly, outside a benchmark you are likely to even be able to notice the difference.
Also, I canot reproduce the extremely poor random write performance with my SSD. This is my result
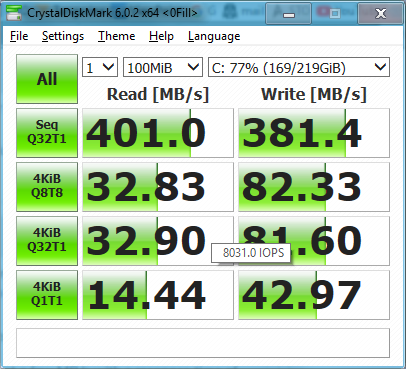
The above result is with VeraCrypt and two Serpent(AES()) chained encryption.
In short, yes, there is an issue. It's not serious. It will likely not affect anyone in the real world. Sequential read/write is essentially unaffected. Random read/write is affected, but not as seriously as you might think. And for most users, you won' t notice a thing.
How is a decrease from a couple hundreds to 45 MB/s read or even 80MB/s for the write "not serious"? The difference is indeed noticeable. I've tried the SSD again unencrypted and this time the SSD wasn't at 100% disk activity with 50 write or read with response times of 3000ms making the OS quite laggy. Games loaded a tad faster as well. I'd say it is pretty serious.
Last edit: wat 2018-12-03
Perhaps I didn't explain this well enough.
The "decrease" you are seeing on the is just a number printed by a disk benchmark program. Benchmarks are only useful insomuch as they represent what happens in the real world. You are simply looking at those numbers and seeing that one is much higher and you are thinking that represents something better. You have to interpret what the number means for the benchmark to be meaningful.
That number represents the number of random reads of 4kb of data that can occur when using multiple threads. Outside of a disk benchmarking environment, it is highly unlikely you will ever encounter this kind of sustained disk activity in the real world. I can't think of a real-world scenario outside of a server environment where you would want to chain together tens of thousands of individual seek/read operations occuring with multiple threads. Even in a server environment almost all software is designed specifically to avoid that kind of behaviour, so as to avoid thrashing a physical drive.
The only reason that kind of thing is even benchmarked is just to show off what a SSD can do that a physical drive can't. It's a way the benchmark crowd pat themselves on the back.
I do not find my OS laggy in the least. I do not find my game load times are adversely affected. In fact, in Star Trek Online, I find I am consistantly the first one in my team to load and enter a mission, and that is a function mostly of client load time.
I did not say VeraCrypt has zero impact on the performance of an SSD system. Just that this issue will have almost no impact on system speed. For most people and situations outside of a benchmark program it will be essentially unnoticable. I will give that there will always be some performance penalty with VeraCrypt, though. No disk encryption system can get around that. Game engines, if they are well written, are designed to do some of the heaviest CPU work during a level load operation in separate processing threads during times of high disk activity in order to minimize load times on systems that have physical hard drives. This is so that the CPU is staying busy processing the level data it has while a separate thread is collecting more. So VeraCrypt is now contending for CPU usage with games that are increasingly written to take advantage of multiple CPU cores. This is not something that "fixing" the minor issue in the VeraCrypt driver is ever going to address. You simply cannot have disk encryption occur at the speed of an SSD without a CPU performance penalty.
So, I stand by my assessment:
Last edit: Kurt Fitzner 2018-12-03
Same problem. This is not about hypothetical benchmarks, but noticable, with the SSD constantly at 100%. When I switched to Bitlocker, the problem went away.
*After encrypting the drive on Windows 10 - *
Did you use that SSD as a volume or the entire boot drive that you encrypted? Just curious.
I have PM981 and just wondering if the problem extends there.