Home
antigift is simple cross-platform, files & folders encryption tool (with ccrypt backend)
antigift could be used for encryption files & folders on USB-flash or HDD partition. Works on Linux (including Android), Windows, Mac OS X, FreeBSD, DragonFly BSD and other on OSes. Do not required installation. Include WIPE tool for wiping free space and tool for recovery forgotten key.
What's new in version 3.0:
- added support for Android;
- by default on Unix-like OSes antigift now use ccrypt, which user need to install from repositry;
- usage binaries of ccrypt which shipped within tar-archive of antigift is still avalable if you change USE_BINARY param of scripts.
Installation:
Download and extract achieve and put files and folders (SYS, INB and CPT) to SD-card or to any other removable drive you have. Also you may extract and use antigift on any HDD partition or you home directory.
For Android you need to setup Termux application from Google Play. Next in the Settings | Apllication | Termux | Permissions and allow Full access to Memory for Termux app. Then run Termux and setup ccrypt from repository: pkg install ccrypt. Next, in Termux, change directory to root of SD-card and run antigift's scripts.
Requirements:
No special requirements on Windows. For Linux (including Android), FreeBSD, DragonFly BSD and Mac OS X you need to install ccrypt from repository. If there is no ccrypt package in repository, you may set USE_BINARY=1, then antigift's scripts whoud use binaries of ccrypt, which placed in SYS directory. Also you may compily ccrypt from sources if run script SYS/REBUILD.sh. On Unixes you may need mount USB flash drive with exec option.
Ideology concept:
Situation when you are saving your private data and public data on one removable drive is quite possible. Messing up private data and public ones makes you be more careless.
If you lost your phone with SD-card, USB drive or forget them in public places, it simply means you gift your data to anyone who will find it. Antigift is a tool which prevents such situation.
But you know what data is your private one and important. Also you know what data is public one. So there are no reasons to encrypt public available data (e.g. video, music, etc) which you could easily download from Internet. So first make yourself to separate your real private data and public ones.
The best of using this tool is that it is simple and you do not bind to non-Open Source software and, as ccrypt is avalable on many platforms, it is possible to use this antigift's scripts and ccrypt as standart tool for your encrypting purposes.
Description of folders and files inside antigift:
INB - inbound folder for private data(for encrypted and decrypted).
SYS - system folder with program ccrypt for different platforms,
CPT - folder with encrypted files,
CRYPT.sh - encryption script for Unix/Linux systems, Mac OS X and Android.
CRYPT.BAT - encryption script for Windows.
DECRYPT.sh - decryption script for Unix/Linux systems, Mac OS X and Android.
DECRYPT.BAT - decryption script for Windows
MISSKEY.sh - for recovery partially forgotten or mistyped key for Unix/Linux, Mac OS X and Android.
MISSKEY.bat - for recovery partially forgotten or mistyped key for Windows.
WIPE.sh - script for wiping free space to clear deleted files on Unix/Linux, Mac OS X and Android.
WIPE.BAT - script for wiping free space to clear deleted files on Windows
Just follow few simple steps to encrypt and decrypt the files or folders.
To encrypt your private data:
- Move (command mv or Cut and Paste in Explorer) your private data to inbound INB/ folder.
- Then click on CRYPT.bat if you have Windows. Run sh ./CRYPT.sh on Linux, MacOS X, Android and on any other OS.
- Wait until encryption finish.
- Your private data will be encrypted and placed to CPT/ folder. Extension of each file will be *.cpt.
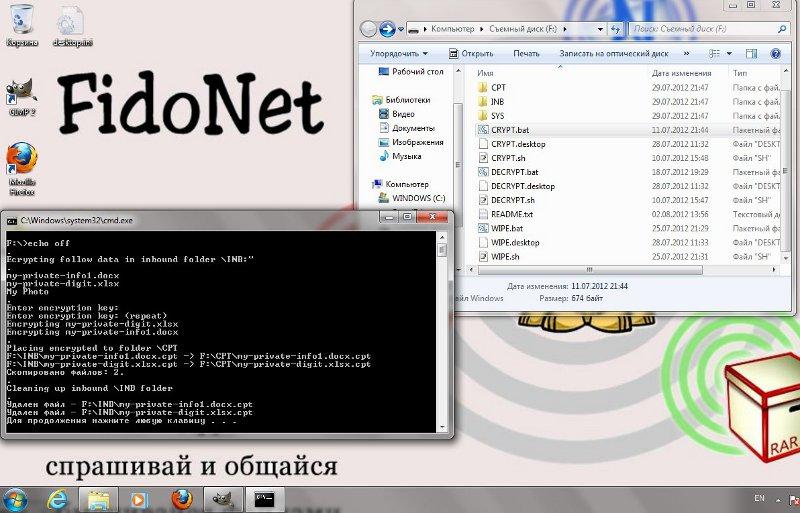
Pic. 1 Encrypting on Windows
Decryption is similar:
- Copy your private encrypted *.cpt files or folders from CPT/ directory to inbound folder INB/.
- Then click on DECRYPT.bat if you have Windows. Run sh ./DECRYPT.sh on Linux, MacOS X, Android and on any other OS.
- Wait until decryption finish.
- Your private data will be decrypted, work with it in inbound folder INB/.
After finishing your work do not forget to encrypt with CRYPT.bat or ./CRYPT.sh again.
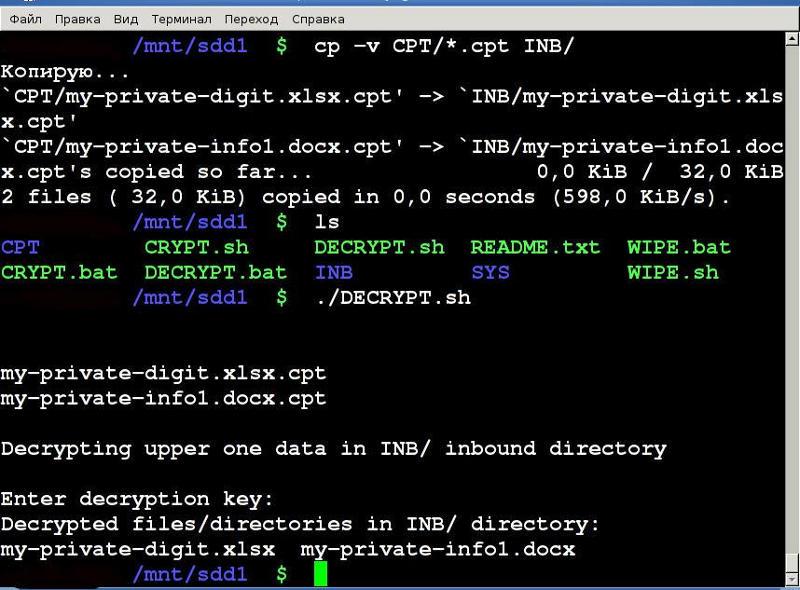
Pic. 2 Decryption in Linux
Recovery of partilly forgotten or mistyped key:
If you entered the wrong part of the key or have forgotten some of the characters entered during password setting combination, then decrypt the data will be very difficult. You have to remember the full and right key combination or try to pick up random keyed characters which is quite time-consuming and boring deal. Antigift includes easy tool which allow automatical brute force part of you key, but only small part. If you make a mistake more then two characters or forget more then 2 letters or number of your key - this tool will be useless. I other cases recovery of forgetten one or two symbols can be done very quickly, the tool will show the correct password in a few second.
To do this:
- Copy the encrypted files *.cpt from the from CPT folder to input folder INB/.
- Then click on MISSKEY.bat, if you work in Windows. Or run sh ./MISSKEY.sh in Linux, Android and any other OS.
- Enter the part of key which you remember and press ENTER.
Wait for the brute forcing of the key will be finished. If you entered key differ by 1-2 characters within a few seconds you will see the right key combination.
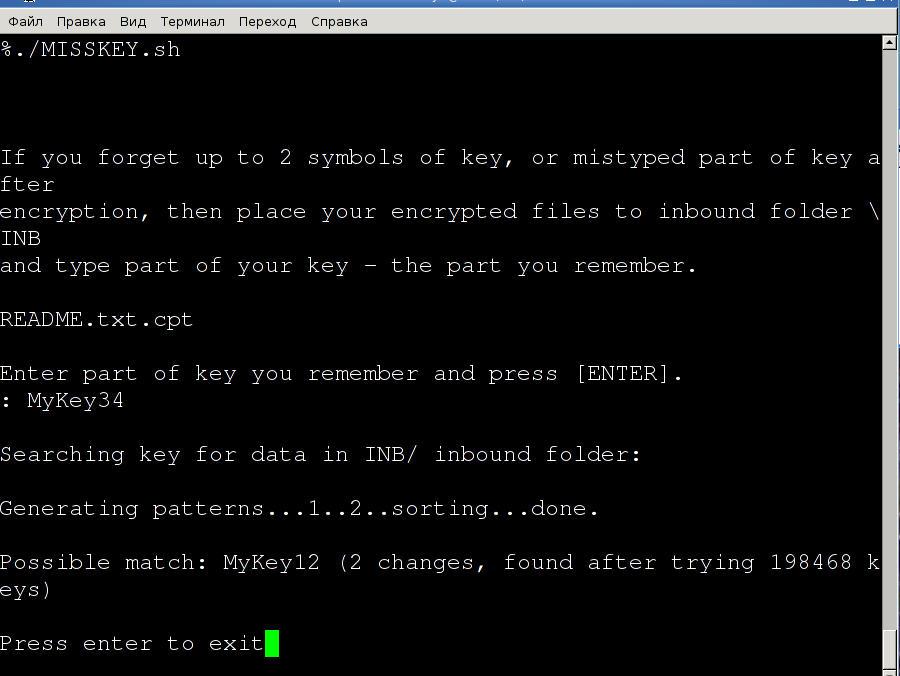
Pic. 3 Recovery of forgotten key in Linux
Then run or DECRYPT.bat or sh ./DECRYPT.sh, enter founded key and decrypt your data.
Wiping data of deleted files:
- Click on WIPE.bat if you have Windows. Run ./WIPE.sh on Linux, MacOS X and on any other OS.
- Wait for wiping data is finished.
Note for wiping out data:
Default behavior of ccrypt (used as backend) is to replace a space on disk which was used for original unencrypted file by encrypted file.
You do not need to wipe out free space with zero if you are using ccrypt.
Just do not forget to move or cut/paste your private data instead copy one.
If you make double copy of original files and then delete it you need to run wiping scripts WIPE.bat or sh ./WIPE.sh.
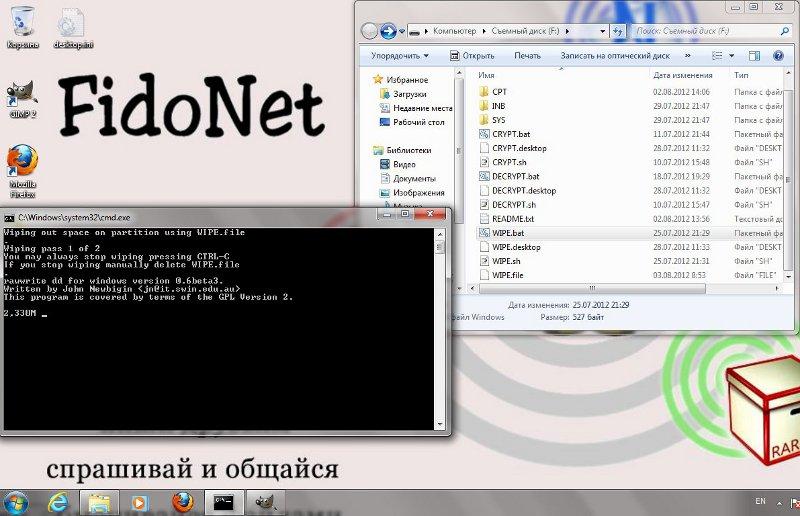
Pic. 4 Wiping out free space on Windows
Note compressing data:
You may compress your private data. But compress your private data before encryption(as after encryption compression will ineffective).
And you need to wipe out your data after you delete uncompressed original files.
Note for recovering damaged data:
If your encrypted file was modified or damaged you could recover it partially using -m switch( --mismatch) of ccrypt utility. Of course it will recover data only from beginning of file to position it was modified. For details please refer to ccrypt documentation.
